Focused offensive cybersecurity solutions fortifying the security posture of organizations.
We are experts in adversarial simulation, advanced persistent threat emulation, penetration testing, red teaming, attack surface analysis, and threat hunting.



Our Services
To combat today’s cybersecurity threats, the best defense is a good offense.
Our cybersecurity consultants will go on the offensive against your environments and help you identify complex security risks and undetected vulnerabilities.
Penetration Testing
Practically gauge the efficacy of security controls, employing an adversarial perspective by simulating an attack.
Vulnerability Assessments
Identify, inventory, and assess potential security centric issues in technology infrastructure, assets and personnel.
Red Teaming
Test your detection and telemetry capabilities leveraging a goal-oriented, targeted, clandestine, opportunistic approach.
Social Engineering
Ascertain your employees resilience to coercion attacks, and gauge gaps in user-awareness that often lead to compromise.
Security Program Engineering
Establish the foundation, then build the framework; the recipe for a robust program meant to protect data and systems.
Cybesecurity Training
Stay up-to-date on the latest tools, techniques, tactics and procedures that adversaries use to compromise environments.
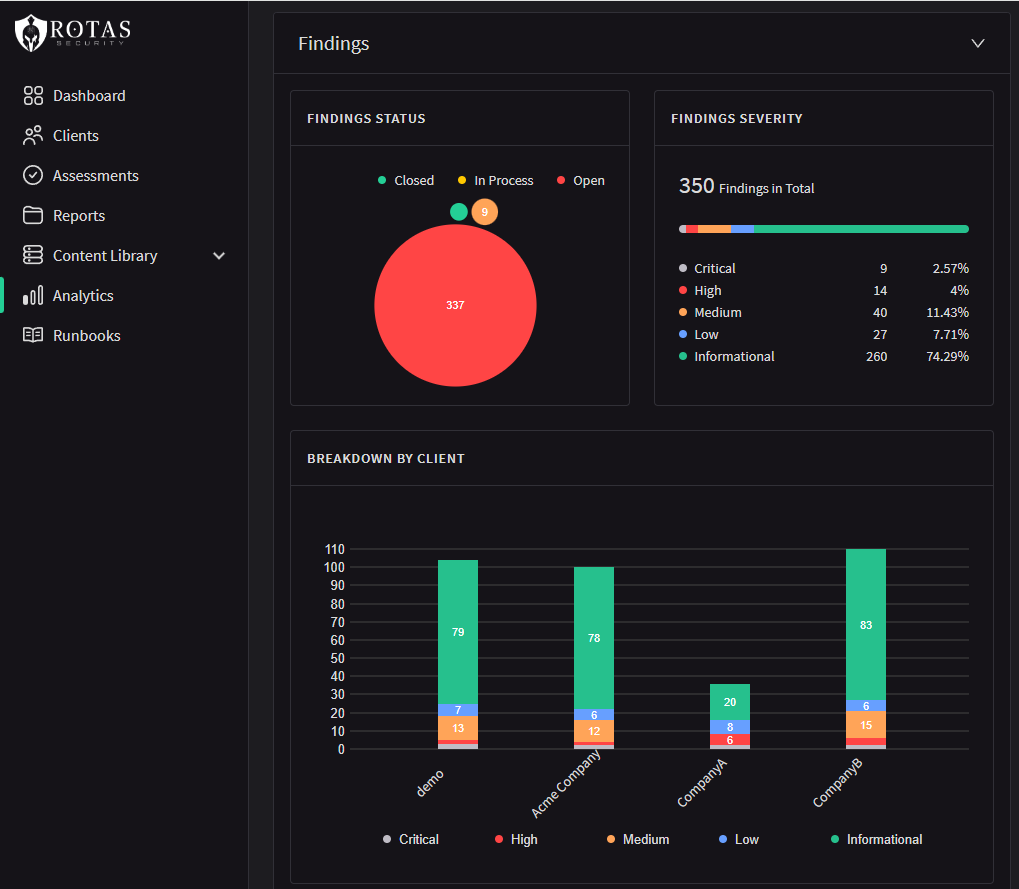
Our REPORTING
Clearly articulated, contextualized reporting that conveys everything you need to fix in order to be secure.
We recognize that a critical aspect of project delivery is to report our findings in easy-to-understand and contextualized terms. Plus, we give you peace of mind by showing the comprehensive nature of our efforts that ensures you we haven’t missed anything.
- Robust, digitally-delivered reports
- Prioritized and highly actionable findings
- Comprehensive to ensure nothing is missed
OUR Resources
The latest cybersecurity insights
Emerging threats and trends, and industry perspectives provided by hackers, leaders and practitioners.





